Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
December 2023
How to prevent open redirect vulnerabilities in Laravel
An open redirect vulnerability occurs when a website allows user-supplied input to influence the destination of a redirect without implementing proper validation or sanitization measures. To exploit this vulnerability, an attacker may send users a seemingly trustworthy link, which, when clicked, redirects them to a harmful website, potentially leading to phishing attacks or other malicious activities.
Command injection in Python: examples and prevention
Despite Python's reputation for simplicity and versatility, ensuring the security of Python programs can be challenging if you or other team members neglect security best practices during development. Additionally, you’ll likely use libraries or other open source projects while building a Python application. However, these resources can introduce additional security issues that leave your program vulnerable to exploits such as command injection.
Is your team on the *security* naughty or nice list?
As kids, many of us felt anticipation, excitement, and maybe even nervousness during the holiday season. Had we been good enough to get the Gameboy, Barbie Dream House, or Etch a Sketch we’d been pining for, or were we just going to get a big ol’ lump of coal?
Vulnerability disclosure: Which comes first, the security bug in PHP or the CVE?
For security researchers, there is a series of hurdles in raising a potential vulnerability well before the issue itself is widely recognized. Convincing the project maintainers that there is an issue becomes the first hurdle, even with a working example. At times, there is a thin and fuzzy line to a vulnerable path being identified as a bug rather than a security vulnerability.
Common SAML vulnerabilities and how to remediate them
Security Assertion Markup Language (SAML) is an XML-based framework that plays a pivotal role in enabling secure identity and access management. It acts as a trusted intermediary between various entities in a digital ecosystem, such as identity providers, service providers, and users. The primary purpose of SAML is to facilitate single sign-on (SSO), a seamless and efficient authentication process where a user can access multiple applications and services using a single set of credentials.
Snyk named as a top cybersecurity company in inaugural Fortune Cyber 60 2023 list
We’re proud that Snyk has been honored with inclusion on the inaugural Fortune Cyber 60 list as a top growth-stage company. The full list was unveiled late last week. In 2023, our industry encountered distinctive challenges, but the entire Snyk community demonstrated resilience and a steadfast commitment to our founding mission: empowering and equipping DevSecOps teams worldwide to build securely.
Top 3 security best practices for handling JWTs
In modern web development, JSON Web Tokens (JWTs) have become a popular method of securely transmitting information between parties. JWTs are used for authentication and authorization and are often used to store user information. However, with the increasing use of JWTs come potential security risks that developers need to be aware of. As a developer, you are responsible for ensuring that your application is secure and user data is protected.
Snyk highlights AWS re:Invent 2023
With over 50,000 in attendance, AWS re:Invent 2023 had generative AI taking center stage at keynotes, race cars, and robots wowing at the Expo. Once again, Snyk showed up in a big way. Some of our highlights included being awarded the AWS ISV Partner of the Year in EMEA and UKI, achieving AWS Security Competency, and several new integrations with AWS services. Best of all, we got to meet all of you!
Enhancing code to cloud security with the Common Configuration Scoring System
Proprietary severity scoring often burdens AppSec teams. With every new vendor, you must evaluate their custom severity framework and work to translate assessed risk between tools. To eliminate this burden and provide our customers with a clear security assessment for configurations across the SDLC, Snyk will be moving towards standardizing our code to cloud security rules set on the Common Configuration Scoring System (CCSS)!
Three reasons to invest in an ASPM solution in 2024
The pace of software development is astounding! The transition to agile, DevOps, cloud, and the supercharged use of AI is empowering distributed development teams to build software with greater speed and autonomy. In contrast to the remarkable strides in development methodologies, maintaining a robust security posture has become a formidable challenge. AppSec teams are still playing catchup, both outnumbered and out-resourced.
Announcing Snyk AppRisk: Elevate your AppSec game with ASPM
Snyk AppRisk provides AppSec teams with the comprehensive application security posture management (ASPM) workbench they need to govern and scale their security programs as well as minimize risk arising from applications.
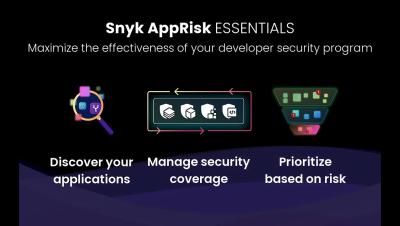
Introducing Snyk AppRisk Essentials
Snyk recognized as an Emerging Segment Leader in Application Security in Snowflake's Next Generation of Cybersecurity Applications report
We are thrilled to announce that Snyk has been acknowledged as a key player in the evolving landscape of application security. The recent release of Snowflake's Next Generation of Cybersecurity Applications report has designated Snyk as an Emerging Segment Leader in Application Security, highlighting our commitment to innovation and excellence in the field.
Code injection in Python: examples and prevention
As software becomes increasingly integral to our professional and personal lives, the need to protect information and systems from malicious attacks grows proportionately. One of the critical threats that Python developers must grapple with is the risk of code injection, a sophisticated and often devastating form of cyberattack.
Accelerate C/ C++ security with Snyk
Securing C/C++ applications has been a massive challenge historically. Until today, many organizations using C/C++ have had to rely on a niche, single-language tool that, while decent at finding vulnerabilities, requires code to be compiled before scanning, slows down developers with clunky integrations, and provides vulnerability alerts that do not help developers to remediate the issue.
Secure password hashing in Go
User credentials are the information required to authenticate a user's identity and grant them access to a system or application. Typically, this includes a username or email address and a password. While a username can be stored as plaintext in a database, sensitive information like email addresses or passwords should not. If a malicious actor gains access to your database where you store this information, you don't want to hand over this information to them easily.
Achieving developer security adoption at Nylas with Snyk
Effective security programs promote collaboration between developers and security teams. Many organizations aim for a seamless developer experience that allows security teams to build guardrails directly into dev workflows, breaking down silos, and promoting collaboration between these departments.
Snyk named a 2023 Gartner Peer Insights Customers' Choice for Application Security Testing
Snyk, the leader in developer security, is excited to share that we’ve been named Customers’ Choice in the 2023 Gartner Peer Insights Voice of the Customer for Application Security Testing for a second consecutive year. Gartner defines the Application Security Testing category as products and services designed to analyze and test applications for security vulnerabilities. This distinction is based on meeting or exceeding user interest, adoption, and overall experience.