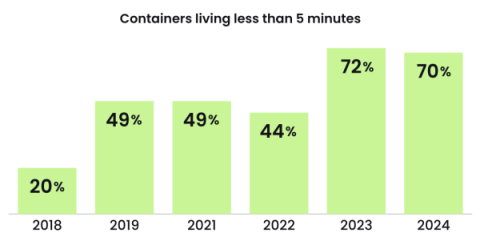
Ephemeral Containers and APTs
The Sysdig Threat Research Team (TRT) published their latest Cloud-Native Security & Usage Report for 2024. As always, the research team managed to shed additional light on critical vulnerabilities inherent in current container security practices.