Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
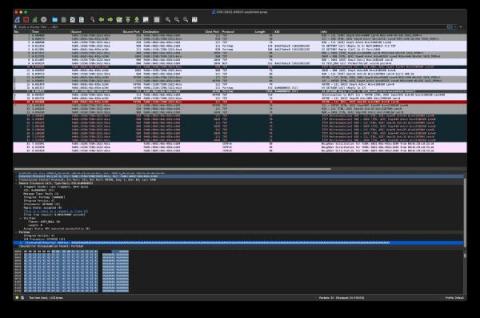
Detecting CVE-2022-26937 with Zeek
This month, Microsoft announced a vulnerability in NFS. The exploit lies in how an attacker can force a victim NFS server to request an address from the attacker’s fake NFS server. The address returned will overflow memory on the victim NFS server and cause a crash. Through Microsoft’s MAPP program, Corelight Labs reviewed a proof-of-concept exploit for this vulnerability and wrote a Zeek®-based detection for it. You can find a PCAP of this exploit in our GitHub repository.
Detecting CVE-2022-23270 in PPTP
This month, Microsoft announced a vulnerability in PPTP, a part of the VPN remote access services on Windows systems that runs on port 1723/tcp. Through Microsoft’s MAPP program, Corelight Labs reviewed a proof of concept exploit for this vulnerability and wrote a Zeek®-based detection for it.
JavaScript Live Panel with Snyk Ambassadors
Are your Apple devices safe from the latest vulnerabilities?
Apple has recently released OS updates for multiple operating systems, addressing known and exploited security vulnerabilities along with previously unknown ones. During the past week, various data security organizations like the US Cybersecurity and Infrastructure Security Agency and Indian Computer Emergency Response Team have issued warnings asking users to install the latest updates on their Apple devices as soon as possible to avoid possible exploitation of devices and device data.
Hack a vulnerable OWASP Node.js app
Performance improvements, snappier ports, and spring cleaning
The vulnerabilities page allows you to see all findings across your attack surface. This includes simple filters that let you specify what you want to focus on, including the level of severity, which domains you want to look at, and whether it was found in the past week or the past month.
Snyk finds 200+ malicious npm packages, including Cobalt Strike dependency confusion attacks
Snyk recently discovered overt 200 malicious packages in the npm registry. While we acknowledge that vulnerability fatigue is an issue for developers, this article is not about the typical case of typosquatting or random malicious package. This article shares the findings of targeted attacks aimed at businesses and corporations that Snyk was able to detect and share the insights.
Credit Card Fraud Investigation: State of Underground Card Shops in 2022
In our latest credit card fraud investigation blog our threat intelligence analysts investigate the current card shop ecosystem, from active shops and the return of Rescator as well as other recently shuttered card shops and credit card fraud to look out for. Methodology Credit Card Fraud Investigation: Active Card Shops Credit Card Fraud Investigation: Inactive Card Shops Conclusions
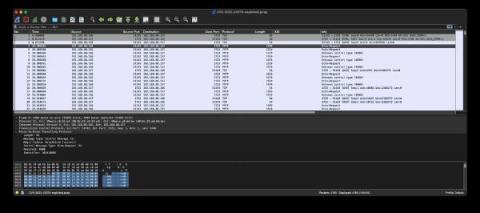
Finding CVE-2022-22954 with Zeek
CISA released a warning to federal agencies on May 18 that APT actors are actively exploiting recent vulnerabilities found in VMware, including CVE-2022-22954. Your first thought may have been to want new signatures, indicators, and/or behavioral techniques to detect attempted and successful exploits. If you’re a Zeek user or Corelight customer, you’ll find that sometimes you’re already getting what you need.