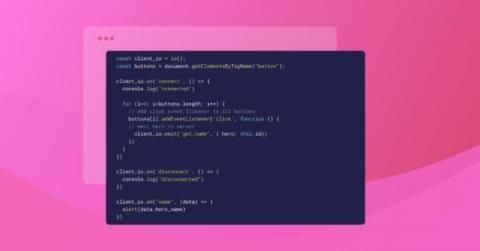
5 Common blind spots that make you vulnerable to supply chain attacks
Over the past several years, hackers have gone from targeting only companies to also targeting their supply chain. One area of particular vulnerability is company software supply chains, which are becoming an increasingly common method of gaining access to valuable business information. A study by Gartner predicted that by 2025, 45% of companies will have experienced a supply chain attack.