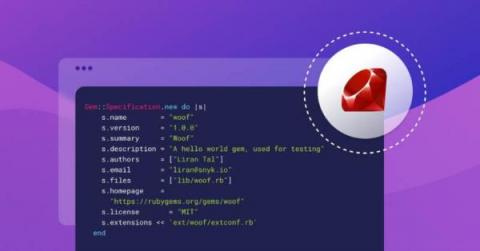
The dangers of assert in Python
There are many ways to find bugs in Python code: the built-in debugger (pdb), a healthy amount of unit tests, a debugger in an IDE like Pycharm or Visual Studio, try/catch statements, if/else statements, assert statements, or the tried and true practice of covering every inch of your codebase in print() statements like it’s going out of style. Assert statements can help us catch bugs quickly and are far less intrusive than copious amounts of print statements.