Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
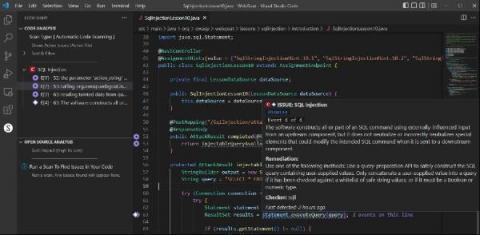
Secure JavaScript URL validation
When developers need to handle URLs in different forms for different purposes — such as browser history navigation, anchored targets, query parameters, and so on — we often turn to Java. However, its frequent use motivates attackers to exploit its vulnerabilities. This risk of exploitation is why we must implement URL validation in our JavaScript applications.
Implementing TLS/SSL in Python
Nowadays, we do virtually everything online: book flights, pay for goods, transfer bank funds, message friends, store documents, and so on. Many things we do require giving out sensitive information like our credit card details and banking information. If a website uses an unsecured network, a malicious hacker can easily steal user information. This is why encryption is so important.
Convince Your Boss You Need These Managed IT Security Services
Considering managed it security services? It is more important than ever to have a resilient security posture. Hackers are constantly looking for ways to exploit weaknesses in systems, and even a small data breach can have devastating consequences.
CVE-2022-40684: Widespread Exploitation of Critical Fortinet Authentication Bypass Vulnerability
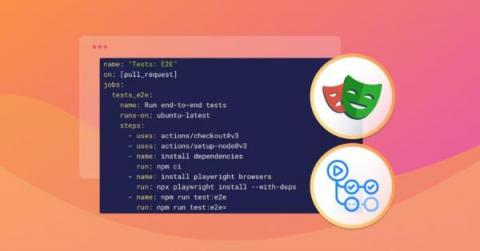
How to add Playwright tests to your pull request CI with GitHub Actions
If you’re like me, you really appreciate a test automation step as part of your pull request (PR) CI for that added confidence before merging code. I want to show you how to add Playwright tests to your PRs and how to tie it all together with a GitHub Actions CI workflow.
Critical Remote Code Execution & Authentication Bypass Vulnerabilities in Aruba EdgeConnect Enterprise Orchestrator
Payment Details of 1.2M Cardholders Leak on the Dark Web
Read also: Microsoft fixes a Windows zero-day, Mango Markets DeFi platform robbed of over $100M, and more.
Ruby email rule removed from Snyk Code
Snyk Code supports various languages important in the cloud native arena, Ruby being among them (and we’ve seen great adoption, so thank you!). Our researchers are constantly monitoring our rule sets, using our training set of open source projects, but also — and, yes this is an advantage of a SaaS service — how the rules do on the code that is scanned. Just as a reminder, Snyk does not use your code to train our sets — but we do aggregate usage statistics.
ModSecurity Request Body Parsing: Recent Bypass Issues
ModSecurity is an open-source web application firewall (WAF) engine maintained by Trustwave. This blog post discusses multiple input interpretation weaknesses in the ModSecurity project. Each input interpretation weakness could allow a malicious actor to evade some ModSecurity rules. Both ModSecurity v2 and ModSecurity v3 were affected. The issues have been addressed in v2.9.6 and v3.0.8, respectively.