Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
Paws in the Pickle Jar: Risk & Vulnerability in the Model-sharing Ecosystem
Integrations 101
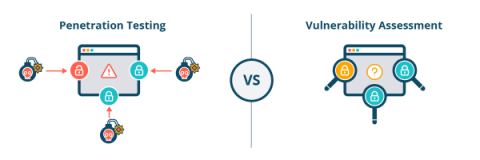
What's the difference: Vulnerability scanning vs Penetration testing
Vulnerability scanning and penetration testing should be an essential part of your cybersecurity strategy. This blog discusses the above methods in the context of securing your web applications, including the benefits, drawbacks, and compliance implications. Table of contents: What is a vulnerability scan? What is a penetration test? What are the drawbacks of the traditional pen test model? Should I only to pen tests, vulnerability scans, or both?
Lessons from OpenSSL vulnerabilities part 2: Finding and fixing supply chain vulnerabilities
This supply chain series centers on the lessons learned from OpenSSL and what you need to consider when enhancing your supply chain security. While this series will focus on OpenSSL and relevant libraries, we'll also consider vulnerabilities across the board. In the first installment, we covered everything you need to know about where to look for vulnerable libraries.
Preventing Cross-Site Scripting (XSS) in Java applications with Snyk Code
Java is a powerful backend programming language that can also be used to write HTML pages for web applications. However, developers must know the potential security risks associated with Cross-Site Scripting (XSS) attacks when creating these pages. With the rise of modern templating frameworks, preventing security attacks through proper input validation and encoding techniques has become easier.
Best Practices for Your First 30 Days, April 2023
SLP: a new DDoS amplification vector in the wild
Earlier today, April 25, 2023, researchers Pedro Umbelino at Bitsight and Marco Lux at Curesec published their discovery of CVE-2023-29552, a new DDoS reflection/amplification attack vector leveraging the SLP protocol. If you are a Cloudflare customer, your services are already protected from this new attack vector.
New high-severity vulnerability (CVE-2023-29552) discovered in the Service Location Protocol (SLP)
Researchers from Bitsight and Curesec have jointly discovered a high-severity vulnerability — tracked as CVE-2023-29552 — in the Service Location Protocol (SLP), a legacy Internet protocol. Attackers exploiting this vulnerability could leverage vulnerable instances to launch massive Denial-of-Service (DoS) amplification attacks with a factor as high as 2200 times, potentially making it one of the largest amplification attacks ever reported.
Reduce resolution time for container vulnerabilities with ServiceNow & Sysdig
Today, security and development teams are drowning in vulnerabilities. Most security tools identify issues, but don’t provide reliable prioritization or simplify remediation. To help solve these challenges, Sysdig runtime vulnerability management – part of Sysdig’s Cloud Native Application Protection Platform (CNAPP) – provides a runtime image scanner coupled with an eBPF probe to analyze container behavior and identify the vulnerable packages that are in use at runtime.