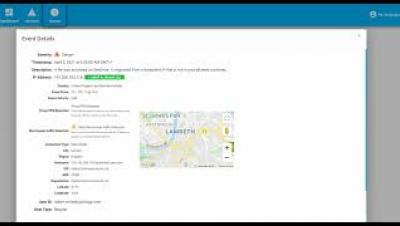
Ingesting threat data with the Threat Intel Filebeat module
The ability for security teams to integrate threat data into their operations substantially helps their organization identify potentially malicious endpoint and network events using indicators identified by other threat research teams. In this blog, we’ll cover how to ingest threat data with the Threat Intel Filebeat module. In future blog posts, we'll cover enriching threat data with the Threat ECS fieldset and operationalizing threat data with Elastic Security.