Bringing cloud native application security full circle
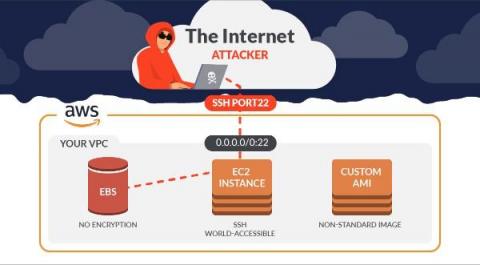
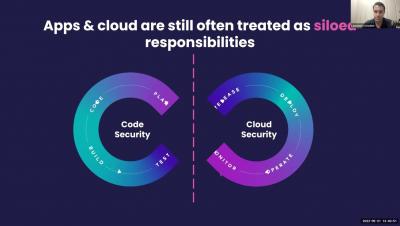
The cloud has enabled organizations to build and deploy applications faster than ever, but security has become more complex. The shift to cloud has created a world where everything is code — not just the applications, but also the infrastructure they run on. So, any security issue within an application or cloud environment can put an entire system at risk. And keeping that cloud native application stack secure is increasingly the responsibility of development teams.