Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Lessons Learnt By An Agent Of Chaos From DevOps
The State of Open Source Security Management RSA 2019
Panel Open Source Security - Weighing the Pros and Cons
Panel Discussion: Forrester's Latest Wave Report on Software Composition Analysis 2019
5G Technology: How to Make Sure the Benefits Outweigh the Security Risks
It’s hard not to say that 5G technology brings a lot of benefits. 5G entails faster download speeds, and yes, if you have a 5G-enabled handset, you could hear and appreciate the speed increases for videos, gaming, etc. However, 5G provides added benefits that go way above those for the everyday user. Let’s take a look at the high speed and low latency of 5G. There are a lot of areas or industries that require pinpoint accuracy and precision.
5 most common mobile phishing tactics
Phishing is one of the things that keeps CISOs up at night. Phishing attacks are effective and simple to launch, and used by financially motivated attackers as well as more targeted attacks. In the case of a targeted attack, it may harvest login credentials to gain access to corporate or personal resources. In fact, sometimes corporate access can be used to steal personal data, and vice versa.
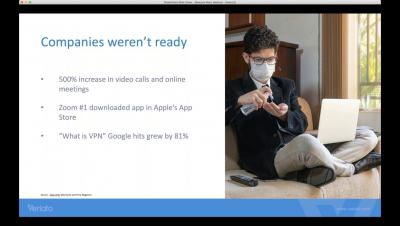
Effectively Managing The Shift To A Remote Workforce
G2 Names Egnyte Top Remote Tool
As businesses adjust to flexible working arrangements amidst stay-at-home orders and social distancing guidelines during the COVID-19 (coronavirus) pandemic, many are looking to technology to support the needs of remote workers. While many companies were already using software to support working outside of physical offices, tools that enable remote working have now become mission critical in many cases to avert disruption during the unprecedented time we find ourselves in.
What is Penetration Testing?
Penetration testing is one of the most efficient and straightforward methods to see how secure your systems are. Read our article to learn how penetration tests are done.