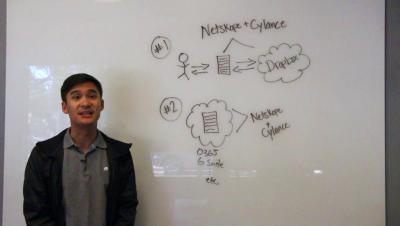
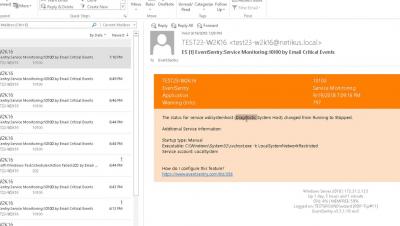
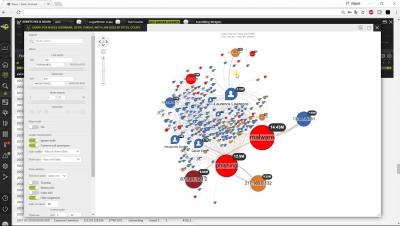
Ten Cool Things Logsign SIEM Does
Easy deployment, an interface to be used intuitively and easily and a rule-based alert, bucket, dashboard and reports are the factors creating the simplicity mindset behind Logsign, who believes in “Simplicity is the ultimate sophistication”. The user interface used for the SOC teams’ threat and anomaly analysis has been designed in order to be understood easily and simply.