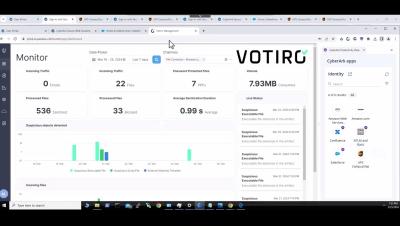
74% of companies do not provide employees with any cybersecurity training
In the digital age, where technology has become indispensable, cybersecurity has become a crucial issue for organizations. Investment in security tools to protect digital assets is increasing; however, the biggest threat often lies in an unexpected factor – human error. Phishing campaigns, weak passwords, or accidental data leaks can put even the most fortified network at risk.