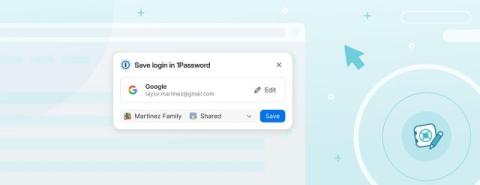
Low-Hanging Fruits Vs. Those at the Top of the Tree: Cybersecurity Edition
Companies often go for high-end cybersecurity solutions because dealing with complex problems looks impressive. The appeal of fancy tech and advanced security challenges gives them a sense of achievement and a chance to show off their skills - and says they're serious about staying ahead of cyber crooks. However, this isn't always the best strategy.