Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Insider Risk Management & User Behavior Monitoring as a Service for an Australian MSP
Fighting Digital Payment Fraudsters in Real-time: A Winning Framework (Part 1)
A few weeks ago Seattle-based financial services and data management firm Automatic Funds Transfer Services (AFTS) suffered a serious ransomware attack. A gang called “Cuba” hacked and stole approximately 20 months’ worth of AFTS data, including financial documents, correspondence with bank employees, account movements, balance sheets, and tax documents. The compromised data then was offered for sale on the dark web.
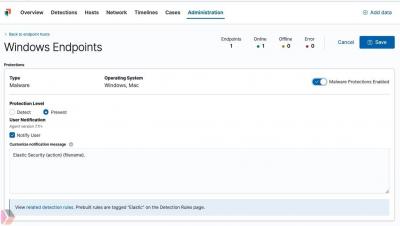
Validating Elastic Common Schema (ECS) fields using Elastic Security detection rules
The Elastic Common Schema (ECS) provides an open, consistent model for structuring your data in the Elastic Stack. By normalizing data to a single common model, you can uniformly examine your data using interactive search, visualizations, and automated analysis. Elastic provides hundreds of integrations that are ECS-compliant out of the box, but ECS also allows you to normalize custom data sources. Normalizing a custom source can be an iterative and sometimes time-intensive process.
Detection and Investigation Using Devo: HAFNIUM 0-day Exploits on Microsoft Exchange Service
On March 2, 2021, Microsoft announced it had detected the use of multiple 0-day exploits in limited and targeted attacks of on-premises versions of Microsoft Exchange Server. The Microsoft Threat Intelligence Center (MSTIC) attributes this campaign—with high confidence—to HAFNIUM, a group assessed to be state-sponsored and operating out of China, based on observed victimology, tactics and procedures.
Key security lessons organisations can learn from recent cloud data breaches
Don't let supply chain security risks poison your organization
Supply chain security risks are not new, but recent headlines are a reminder for consumers to re-examine their security practices. The story about the guy who hit his mule between the eyes with a 2×4 to “get his attention first” so the beast would then obey his gently whispered commands is memorable because it uses humor to make a serious point: Don’t wait to get clobbered before you pay attention to exhortations about what you ought to do.
CMMC vs NIST: What's the Difference?
If your firm is a government contractor working with the U.S. Department of Defense, or works anywhere in the DoD supply chain, brace for big changes in the cybersecurity requirements your business will need to meet. By 2026, the Defense Department will require its contractors to comply with new cybersecurity standards known as the Cybersecurity Maturity Model Certification — CMMC, for short.
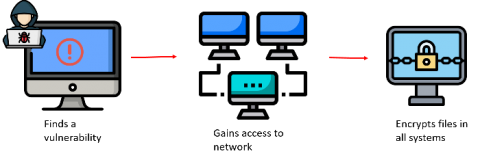
Ransomware in 2021: What has changed? Detection and mitigation strategy
A ransomware attack is a bug that we can’t shake off. Or perhaps, it can even be called a shape-shifter that somehow finds a way into networks, no matter how many armed sentries you’ve deployed in and around your perimeter. The line between ransomware and a data breach is slowly fading. Threat actors prefer ransomware over other modes of attack because they work.
Deepfake cyberthreats - The next evolution
In 2019, we published an article about deepfakes and the technology behind them. At the time, the potential criminal applications of this technology were limited. Since then, research published in Crime Science has delved into the topic in-depth. The study identified several potential criminal applications for deepfakes. Among these categories, the following were deemed the highest risk: This list sparked the idea for this article.