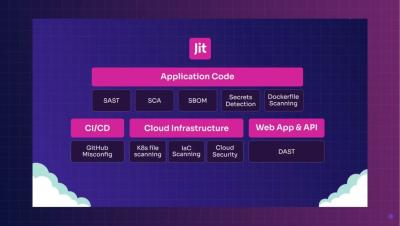
Announcing GitLab support: Empower developers to secure everything they code in GitLab
Today, I’m thrilled to announce Jit’s full support for GitLab, which will significantly expand our ability to execute our mission to empower every developer to secure everything they code. This new integration will provide all of the same benefits that we’ve been delivering to our customers on GitHub for years, including: If you’re on GitLab, check out the guidelines below to quickly realize these benefits.