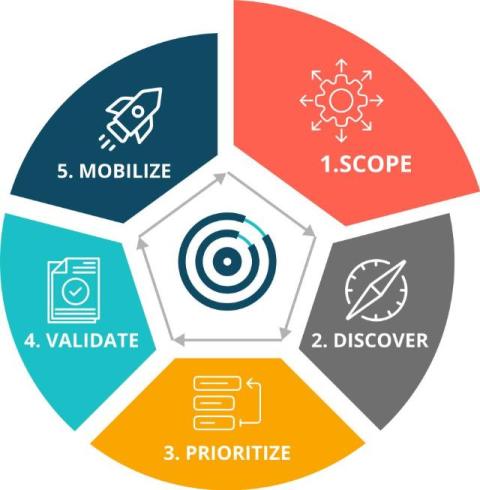
How Automation and AI are Transforming GRC Management
There is no doubt that we now live in an AI-driven, automation-powered world. Across industries and markets, leaders and professionals are achieving the utility of AI in their processes. The same applies to Governance, Risk, and Compliance (GRC) management, but when one looks at the actual implementation, the data shows that there's still a long way to go. According to one recent report, only 21% of GRC leaders use AI to perform GRC activities.