Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
CyberArk
LLMs Gone Wild: AI Without Guardrails
From the moment ChatGPT was released to the public, offensive actors started looking to use this new wealth of knowledge to further nefarious activities. Many of the controls we have become familiar with didn’t exist in its early stages. The ability to request malicious code or the process to execute an advanced attack was there for the asking from an open prompt. This proved that the models could provide adversarial recommendations and new attacks never before seen.
EP 61 - Put Your Name on It: Identity Verification and Fighting Fraud
Aaron Painter, CEO of NameTag, joins host David Puner for a conversation that covers several key themes, including the inadequacies of current identity verification methods, the rise of deep fakes and AI-generated fraud – and the importance of preventing identity fraud rather than merely detecting it. Aaron discusses the role of advanced technologies like cryptography, biometrics and AI in improving identity verification.
CyberArk Recognized as a Leader in 2024 Gartner Magic Quadrant for PAM
Today, we’re exceptionally proud to announce our recognition as a Leader in the “2024 Gartner Magic Quadrant for Privileged Access Management (PAM)”1 for the sixth time in a row. CyberArk was positioned furthest in Completeness of Vision.
Protect Every Identity with CyberArk's Intelligent Privilege Controls | CyberArk
In today's world, more employees than ever—across IT, workforce users, developers, and even machine identities—require access to sensitive data, increasing the risk of identity-based cyberattacks. With over 90% of organizations falling victim to such attacks, securing every identity is critical. Enter CyberArk's Intelligent Privilege Controls. These dynamic security measures adapt in real-time to protect high-risk access, ensuring the right users access the right information at the right time.
How Overreliance on EDR is Failing Healthcare Providers
Ransomware attacks have a profound impact on healthcare organizations, extending well beyond financial losses and the disrupted sleep of staff and shareholders. A University of Minnesota School of Public Health study highlighted by The HIPAA Journal reveals that these attacks can lead to higher in-hospital mortality rates for patients admitted during the incidents. Additionally, the study found that hospital volumes dropped by 17%-25% during the first week of an attack.
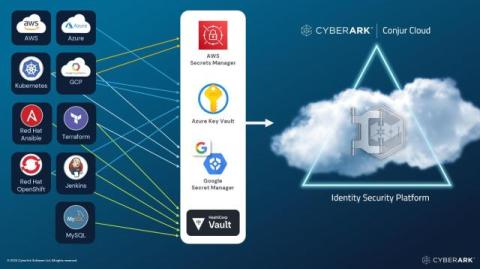
Taming Vault Sprawl with Modern Secrets Management
In this cloud, DevOps and AI era, security teams grapple with the growing challenge of shadow secrets and vault sprawl. As organizations scale, secrets management increasingly fragments. For example, Microsoft recommends using one Azure Key Vault, per application, per environment per region. Without centralized visibility, security policies and rotation control, vault sprawl leads to heightened security risk and compliance challenges.
EP 60 - Going Viral: Security Insights from TikTok's Former Global CSO
In this episode of the Trust Issues podcast, Roland Cloutier, who served as TikTok’s Global Chief Security Officer (CSO) from April 2020 to September 2022, joins host David Puner for a discussion that covers his extensive experience in the field of security. He previously held similar roles at ADP and EMC and is now a partner at the Business Protection Group.
Applying a 'Three-Box Solution' to Identity Security Strategies
Physical and network barriers that once separated corporate environments from the outside world no longer exist. In this new technological age defined by hybrid, multi-cloud and SaaS, identities are the perimeter. Any one identity—workforce, IT, developer or machine—can become an attack path to an organization’s most valuable assets.