Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Vulnerability Remediation Tracking
Vulnerability remediation tracking is one of the important components of cyber security practices. In this blog post, we gathered all the necessary information you must have in regards to this topic.
Love your enemies before you destroy them
The cutting edge of cybersecurity is moving away from a reactive defense. Instead of analysts waiting for a threat to happen, they are proactively searching out attackers in their environment. Attackers are dynamic. They are always changing and improving their capabilities, which means that defenders need to lean in and adapt even faster to keep up. Proactive defense is about predicting, understanding, and preventing as many moves as possible that an attacker could make against you.
Teleport Overview Webinar
How to: On-premise Server Update
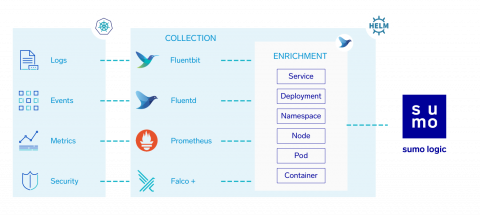
Kubernetes DevSecOps with Sumo Logic
What is CVE? Common Vulnerabilities and Exposures Explained
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed information security vulnerabilities and exposures. CVE was launched in 1999 by the MITRE corporation to identify and categorize vulnerabilities in software and firmware. CVE provides a free dictionary for organizations to improve their cyber security. MITRE is a nonprofit that operates federally funded research and development centers in the United States.
What's new in OTX
Alien Labs and the Open Threat Exchange (OTX) development team have been hard at work, continuing our development of the OTX platform. As some of you may have noticed, we’ve added some exciting new features and capabilities this last year to improve understanding within the OTX community of evolving and emerging threats.
What is Email Spoofing?
Email spoofing is the creation of emails with a forged sender address. Because core email protocols lack authentication, phishing attacks and spam emails can spoof the email header to mislead the recipient about the sender of the email. The goal of email spoofing is to get recipients to open, respond and engage with the email message. Email spoofing can greatly increase the effectiveness of phishing and other email-based cyber attacks by tricking the recipient into trusting the email and its sender.
Ransomware victim hacks attacker, turning the tables by stealing decryption keys
Normally it works like this. Someone gets infected by ransomware, and then they pay the ransom. The victim then licks their wounds and hopefully learns something from the experience. And that’s what happened to Tobias Frömel, a German developer and web designer who found himself paying a Bitcoin ransom of 670 Euros (US $735) after his QNAP NAS drive was hit by the Muhstik ransomware.