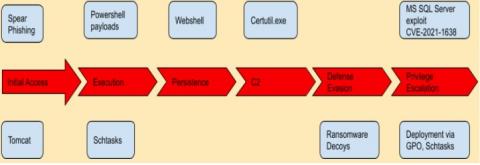
Detecting HermeticWiper
As stated in our previous threat advisory STRT-TA02 in regards to destructive software, past historical data suggests that for malicious actors to succeed in long-standing campaigns they must improve and add new ways of making their payloads stealthier, resistant, and damaging. HermeticWiper introduces some unique features, applying destructive actions on compromised hosts.