Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Splunk
Splunk TV - TV Power User Demo
Splunk SOAR Playbooks: TruSTAR Indicator Enrichment
Slack: Turning Data into Doing
Splunk Live Chat with The Hill: Cybersecurity Trends in the Public Sector
Listen To Those Pipes: Part 2
This blog post is part thirty of the "Hunting with Splunk: The Basics" series. Shannon Davis provided the first half of this blog on pipe hunting in part twenty-nine, and will now run through the second half! – Ryan Kovar
Listen To Those Pipes: Part 1
If you haven’t already read the episode on process hunting, I recommend that you go back and do so, at least for a couple of my jokes, and to help keep our clicks/metrics up. Where that episode concentrated on tracking processes, this blog will concentrate on, you guessed it, pipes. And due to the depth I tried to go with this one, it has been split into a two-part series, so make sure to come back for the second part after you’ve finished this one.
Splunk For OT Security: Perimeter And Vulnerability Evolution
Owners and operators of Operational Technology (OT) environments are being increasingly tasked with providing more information and security controls for their OT Environments, whether those demands are driven by the board, executive orders, or new regulations. One of the biggest fallacies that we encounter when our customers begin monitoring their OT environment is the idea that OT systems are air gapped and completely isolated from IT systems.
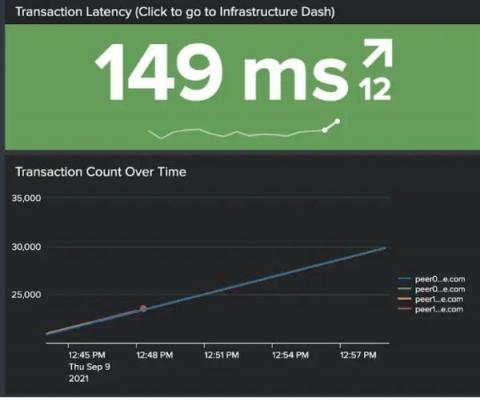
Hyperledger Fabric Security Monitoring with Splunk
In this post, we demonstrate how to set up effective security monitoring of your Hyperledger Fabric infrastructure. We identify some common threats, recognize key data sources to monitor, and walk through using Splunk to ingest and visualize your data. This post follows Introducing Splunk App for Hyperledger Fabric and highlights the use of the app for security monitoring of blockchain infrastructure. We will address smart contract/chaincode security & monitoring in a follow-up post.