Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Corelight
The best cybersecurity defense is great evidence
The saying “data is king” has been around for quite a while and we all know that the world operates and makes decisions on digital data 24x7x365. But, is data king in the field of cybersecurity? I believe that evidence - not data - is what is needed to speed defenders’ knowledge and response capabilities, so let's talk about both.
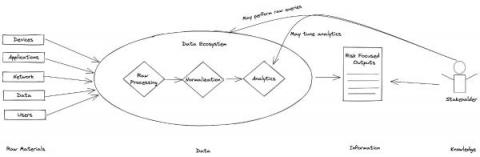
The evidence bank: leveraging security's most valuable asset
Evidence is the currency cyber defenders use to pay down security debt, balancing the value equation between adversaries and the enterprise. Defenders can use evidence proactively, identifying and protecting structural risks within our zone of control. Evidence can also be used reactively by supporting detection (re)engineering, response, and recovery activities, guiding us back to identifying and protecting structural risks.
Enhanced Network Evidence for the Modern SOC
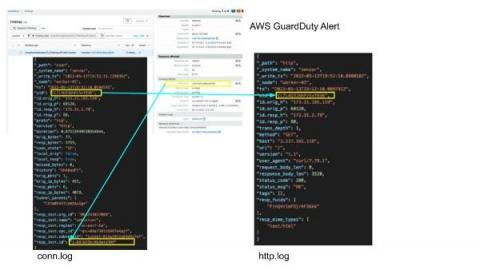
Enriching NDR logs with context
In this post, we show how enriching Zeek® logs with cloud and container context makes it much faster to tie interesting activity to the container or cloud asset involved.In cloud or container environments, layer 3 networking is abstracted away from the higher-level tasks of running workloads or presenting data. Because of this abstraction, when Zeek logs are collected for cloud or container network environments, the attribution of a network flow to actual workload or application is difficult.
Real world use cases for NDR in the Cloud
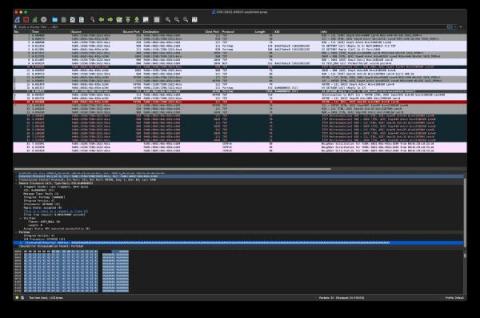
Detecting CVE-2022-26937 with Zeek
This month, Microsoft announced a vulnerability in NFS. The exploit lies in how an attacker can force a victim NFS server to request an address from the attacker’s fake NFS server. The address returned will overflow memory on the victim NFS server and cause a crash. Through Microsoft’s MAPP program, Corelight Labs reviewed a proof-of-concept exploit for this vulnerability and wrote a Zeek®-based detection for it. You can find a PCAP of this exploit in our GitHub repository.
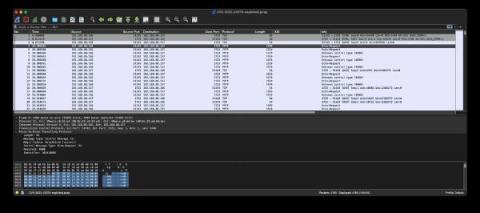
Detecting CVE-2022-23270 in PPTP
This month, Microsoft announced a vulnerability in PPTP, a part of the VPN remote access services on Windows systems that runs on port 1723/tcp. Through Microsoft’s MAPP program, Corelight Labs reviewed a proof of concept exploit for this vulnerability and wrote a Zeek®-based detection for it.
Corelight Investigator accelerates threat hunting
This morning we announced Corelight Investigator, an open NDR platform that enables security teams with the next-level evidence they need to disrupt attacks and accelerate threat hunting through an easy-to-use, quick-to-deploy SaaS solution. How does it work? Investigator combines battle-tested network evidence with intelligent alert scoring to deliver prioritized alerts tied to correlated evidence, enabling analysts to cut through the queue and accelerate incident response.