Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Corelight
Explore Corelight evidence in Humio Community Edition
Now available: A free and easy way to learn about Humio and Corelight. As part of our alliance partnership with CrowdStrike and Humio, Corelight is excited to announce a new collaboration that allows our customers and the community to experience the value of evidence.
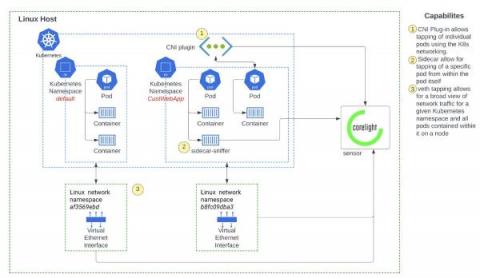
Deeper visibility into Kubernetes environments with network monitoring
Network monitoring solutions can overcome the security visibility blind spots in Kubernetes environments, by providing a source of truth for SOC analysts. Container security solutions broadly span the spectrum of (a) prevention - securing the container image and ensuring the right policies are in place during runtime and (b) detection - monitoring runtime events for threat detection and investigation.
Don't trust. Verify with evidence.
What matters most in a criminal trial? Evidence. Everything depends on the quality and depth of facts deployed to build a case for innocence or guilt. Without compelling evidence, no jury can draw accurate conclusions.
VPNs are increasingly common - how much can you see?
VPN tunnels are like shipping containers in that they are widely used (especially as the pandemic has moved more of the workforce to remote work), and they can be used to carry traffic for legitimate as well as malicious purposes. Establishing a tunnel between corporate offices, remote workers, or partners to transfer data is a legitimate and common use for VPNs.
SANS 2022 Cloud Security Survey
[Webcast] Defending against nation-state actors
SANS 2022 Ransomware Defense Report
Know your environment: Tenable/Corelight integration for prioritized IDS alerts
One of the major causes of alert fatigue for SOCs is a class of alerts that fall in between false positives and useful detections: when an actual attack has been launched, and the detection is working correctly, but the host on the receiving end is not vulnerable, guaranteeing that the attack will fail.
One SIEM is not enough?
The idea behind the SIEM (and now XDR!) technologies was to provide a single engine at the heart of the SOC, aggregating data, enabling analytics and powering workflow automation. The SIEM would act as one place to train analysts and integrate a range of complementary technologies and processes. Given the efficiency that comes from centralization, I was surprised to hear that a growing number of defenders are actually using two SIEMs. Why is that?