Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
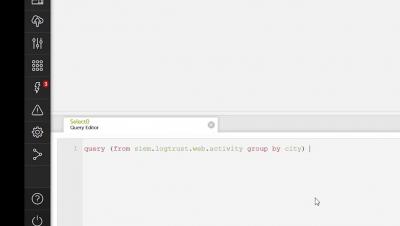
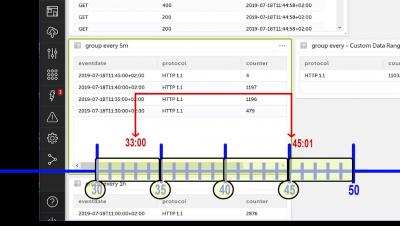
Activeboards [8] - Activeboards Calendars
BlueKeep: What you Need to Know
BlueKeep is the name that has been given to a security vulnerability that was discovered earlier this year in some versions of Microsoft Windows’ implementation of the Remote Desktop Protocol (RDP). The vulnerability was described as “wormable” by Microsoft, and users were warned that BlueKeep might be exploited in a similar fashion to how the WannaCry ransomware used the Eternal Blue vulnerability to spread widely in 2017.
What Is NIST's Cybersecurity Framework Manufacturing Profile?
Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” directed the development of the voluntary Cybersecurity Framework that provides a prioritized, flexible, repeatable, performance-based and cost-effective approach to manage cybersecurity risk for those processes, information and systems directly involved in the delivery of critical infrastructure services.
8 Best Incident Response Use Cases
Incident response is a well-organized approach used in organizations’ IT departments in order to combat and manage the aftermath of a cyberattack or a security breach. The purpose of using incident response is to get out of the nightmare that includes limiting the damage and reducing the costs and recovery time of the incident. The people who perform incident response are called Computer Security Incident Response Team (CSIRT) and they follow company’s Incident Response Plan (IRP).
Moving to the Cloud to Save Money? Think Again...
When I meet with customers, I always ask about their primary objective in moving to the cloud. The majority of these customers have the same response: “to save money.” I can’t blame customers for taking this position. Google “cloud deployment” and the headers are dominated by positive articles that offer up anecdotal evidence of how the cloud can save customers money.
Weekly Cyber Security News 08/11/2019
A selection of this week’s more interesting vulnerability disclosures and cyber security news. A report on the absolutely tragic death resulting from failed safety systems. All I can say is there needs to be oversight on what decisions designers put on how automatous safety systems work in these environments.
What is Protected Health Information (PHI)?
Protected health information (PHI) is any information about health status, provision of health care or payment for health care that is created or collected by a covered entity, or their business associate, and can be linked to a specific individual. The Health Insurance Portability and Accountability Act of 1996 (HIPAA) requires covered entities to implement safeguards to ensure the confidentiality, integrity and availability of PHI.
Max Aulakh | Interviews | Michael Fulton | AVP IT Strategy and Innovation | Nationwide
Data Protection Officer (DPO)
A Data Protection Officer (DPO) is a role that oversees a company’s processing of personal data of staff, customers or any other data subjects to ensure it is done in accordance with the relevant data protection laws. A DPO effectively acts as a bridge between your company and data subjects as well as the ICO (or relevant regulatory authority).