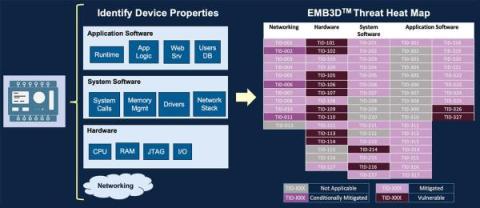
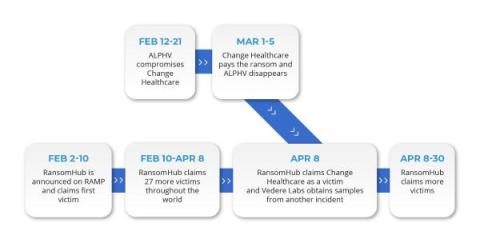
What are the riskiest connected devices right now?
By 2028, connected Internet of Things (IoT) devices will expand to over 25 billion. Yet, today’s connected devices are raising the stakes for assessing risk and managing cybersecurity. They have significantly expanded the attack surface creating new challenges and vulnerabilities. The need for accurate, rapid information from systems across every industry is essential for business operations.