Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
CrowdStrike
CrowdStrike Cloud Infrastructure Entitlement Management (CIEM)
Make Cloud Defense a Team Sport by Turning DevOps into a Force Multiplier
Enterprises are embracing cloud-native applications in the name of business agility. These applications enable developers to take advantage of the cloud’s scalability and flexibility, allow customers and developers to benefit from the increased velocity of DevOps processes and help businesses quickly react to customer needs and potentially lower their cost of deployment.
'Tis the season of eCrime
How CrowdStrike Detects Cloud Storage Misconfigurations to Protect Valuable Data
Cloud storage misconfigurations continue to become more prevalent and problematic for organizations as they expand their cloud infrastructure, driving the importance of technologies such as cloud security posture management (CSPM) as crucial tools for protectors everywhere. Consider the recently reported public exposure of data associated with some Microsoft customers and prospects.
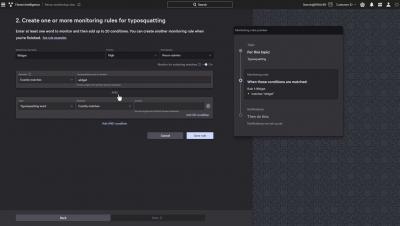
Evicting Typosquatters: How CrowdStrike Protects Against Domain Impersonations
Threat actors constantly unleash phishing attacks that use emails or text messages containing domains or URLs, all designed to impersonate well-known companies and trick users into visiting fake websites and entering their logon or other confidential information. Unfortunately, many users fall prey to such attacks, unknowingly giving threat actors access to their work or personal accounts.
CrowdStrike Achieves 99% Detection Coverage in First-Ever MITRE Engenuity ATT&CK Evaluations for Security Service Providers
The Force Multiplier of Correlating Your Security Telemetry
Consider this situation: A man talks on the phone with a known bank robber. He then rents a building next to a bank. Next, he buys duct tape and ski masks. Any one of these actions could be a red flag alerting police to a potential robbery. But together, they tell a more complete story of a crime in the making. Similarly, in cybersecurity, any single suspicious activity is worth investigating.