Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
CrowdStrike
Under the Wing: Comm100 Supply Chain Attack
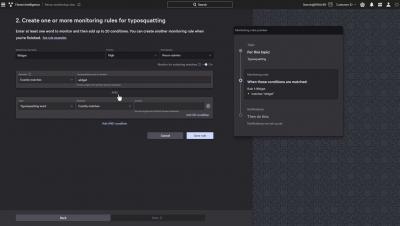
CrowdStrike's Approach to Artificial Intelligence and Machine Learning
How Falcon OverWatch Hunts for Out-of-Band Application Security Testing
CrowdStrike Falcon OverWatch™ threat hunters frequently uncover security testing activity in the course of routine hunting. While much of this activity can be confidently attributed to planned and sanctioned testing, OverWatch is always careful not to discount a threat on the basis that it looks like a test. Some of the more stealthy adversaries will attempt to evade detection by mimicking or using tools and techniques commonly used by security testers.
Importing Logs with CrowdStrike Falcon LogScale Log Collector
For this how-to guide, we’ll walk through how to use the CrowdStrike Falcon LogScale Log Collector to collect and send log events to your CrowdStrike Falcon® LogScale repository. Although the log shipper supports several types of log sources (see the list here), we’ll cover the use case of collecting log events from journald.
How to Complete Your LogScale Observability Strategy with Grafana
CrowdStrike Falcon® LogScale, formerly known as Humio, provides a full range of dashboarding and live query capabilities out of the box. Sometimes, however, you’ll work in an environment where there are other solutions alongside LogScale. For example, let’s say your operations team takes an observability approach that includes metrics scraped by Prometheus, tracing with Jaeger, and dashboard visualizations with Grafana.
Cybersecurity Awareness Month 2022: It's About the People
The theme for Cybersecurity Awareness Month 2022 is “See Yourself in Cyber.” As Cybersecurity Awareness Month comes to a close, CrowdStrike celebrates the many ways human expertise and technology come together to create a stronger defense against adversaries.
Discovering the Critical OpenSSL Vulnerability with the CrowdStrike Falcon Platform
OpenSSL.org has announced that an updated version of its OpenSSL software package (version 3.0.7) will be released on November 1, 2022. This update contains a fix for a yet-to-be-disclosed security issue with a severity rating of “critical” that affects OpenSSL versions above 3.0.0 and below the patched version of 3.0.7, as well as applications with an affected OpenSSL library embedded.
From Data to Deployment: How Human Expertise Maximizes Detection Efficacy Across the Machine Learning Lifecycle
Security is a data problem. One of the most touted benefits of artificial intelligence (AI) and machine learning (ML) is the speed at which they can analyze potentially millions of events and derive patterns out of terabytes of files. Computational technology has progressed to the point where computers can process data millions of times faster than a human could.
Falcon Insight XDR and Falcon LogScale: What You Need to Know
CrowdStrike Falcon Insight XDR™ and CrowdStrike Falcon LogScale™ were hot topics at Fal.Con 2022. We weren’t surprised — both are transformational technologies. They’re also complementary, which spurred some questions about how they work together to solve the toughest IT and security challenges. Here, we dig into the details and clear up some common questions about what these tools do, when they should be used and the value they provide.