Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
CrowdStrike
CrowdStrike Announces Falcon LogScale and Falcon Complete LogScale
Every second, as your IT systems run every facet of your business, they are also creating data related to the health, performance and security of the systems themselves. This information, known as log data, is vital to SecOps, ITOps and DevOps teams as they seek to understand how the IT environment is functioning — and how secure those assets are.
CrowdStrike to Acquire Reposify to Reduce Risk Across the External Attack Surface and Fortify Customer Security Postures
The digital footprint of the modern organization is expanding at an unprecedented rate. The move to the cloud, Internet of Things (IoT), digital transformation, connected supply chain partners and related trends have led to an explosion of internet-facing assets. Cloud workloads, websites, user credentials, S3 buckets, SSL certificates, IoT, operational technology (OT), rogue IT devices, and more exist in the thousands across most organizations.
Welcome to Fal.Con 2022: CrowdStrike Drives the Convergence of Security and Observability
At CrowdStrike, we stop breaches. It’s a simple yet powerful promise to our customers, our partners and to the world. As thousands join us today in person at Fal.Con 2022 in Las Vegas, and thousands more watch remotely via livestream, it’s a promise that we want to reinforce and extend. As cyberattacks have grown more powerful and disruptive, the importance of stopping the breach has grown. Stopping the breach is about more than stopping a single attack.
How to Defend Against Threats with Falcon Intelligence
CrowdStrike Falcon Intelligence Recon
Nowhere to Hide: 2022 CrowdStrike Falcon Overwatch Threat Hunting Report
CrowdStrike Powered Service Providers
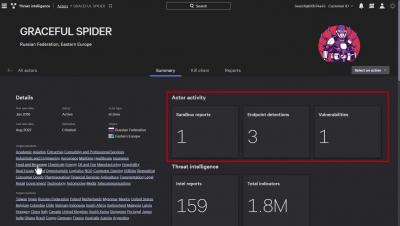
CrowdStrike's Annual Threat Hunting Report Reveals One Potential Intrusion Is Identified Every Seven Minutes
2022 Threat Hunting Report: Falcon OverWatch Looks Back to Prepare Defenders for Tomorrow's Adversaries
Another turbulent year for cybersecurity finds itself right at home alongside global economic headwinds and geopolitical tensions. This year has been defined by rampant affiliate activity, a seemingly endless stream of new vulnerabilities and exploits, and the widespread abuse of valid credentials. These circumstances have conspired to drive a 50% increase in interactive intrusion activity tracked by CrowdStrike Falcon OverWatch™ threat hunters this year.