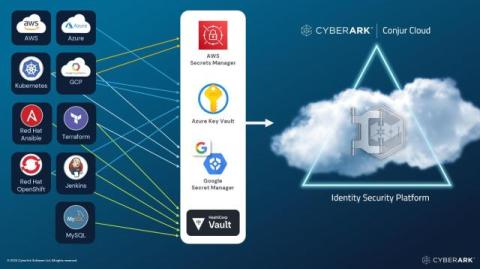
How To Get There: Bridging The Technology Gap Preventing You From Adopting A Secrets-free Machine Identity Framework
Learn how GitGuardian can help you go from a world of secrets sprawl to a future with secrets-free machine identity frameworks by adopting SPIFFE/SPIRE.