Package Provenance: Know the origin
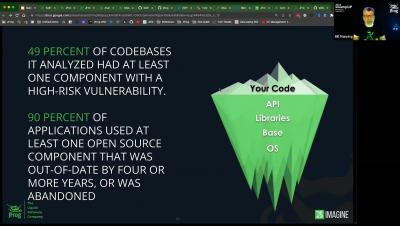
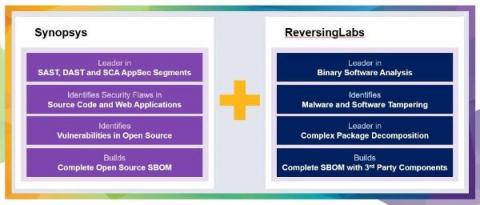
In an era where high-profile security incidents involving the software supply chain have become all too common, the need for robust tools and practices to secure the software we rely on has never been more evident. One crucial aspect of ensuring supply chain security is package provenance, which allows for the tracking of the origin and authenticity of software packages.