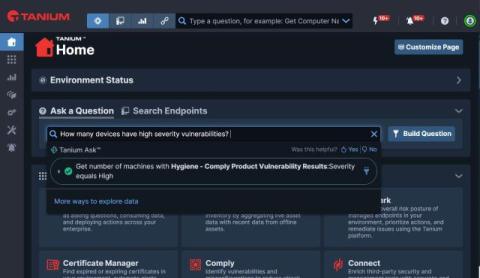
Introducing Tanium Ask: Using AI to Get Questions Answered
How many questions does your organization need to answer about your endpoints every day, and how long does it typically take to get the answer? How often do these questions require an operator with great expertise to provide accurate answers? Do the questions feel like they are resulting in fire drills for your teams?