Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Snyk
This Week in VulnDB
Cheat sheet: Meeting security compliance standards
Security and compliance has a major role in every organization. Businesses are nothing without the trust and loyalty of their customers, and for many companies — from early-stage startups to multinational corporations — winning that trust starts by demonstrating that you have the correct security controls in place. Internationally-recognized compliance standards, such as ISO 27001, PCI-DSS, and SOC 2, make up the industry-standard goals that most businesses and organizations pursue.
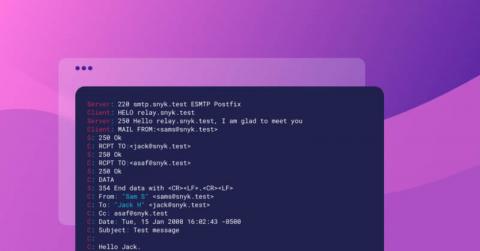
Avoiding SMTP Injection: A Whitebox primer
SMTP Injection vulnerabilities are often misunderstood by developers and security professionals, and missed by static analysis products. This blog will discuss how common SMTP Injection vulnerabilities can exist in libraries and applications, and provide tips for finding and remediating them quickly.
10 best practices to containerize Node.js web applications with Docker
September 14, 2022: Check out our new and improved cheat sheet for containerizing Node.js web applications with Docker! Are you looking for best practices on how to build Node.js Docker images for your web applications? Then you’ve come to the right place! The following article provides production-grade guidelines for building optimized and secure Node.js Docker images. You’ll find it helpful regardless of the Node.js application you aim to build.
Stranger Danger: Your JavaScript Attack Surface Just Got Bigger
Snyk's State of Cloud Security Report Reveals 80% of Organizations Have Experienced a Severe Cloud Security Incident in Past Year
Announcing the 2022 State of Cloud Security report from Snyk
Cloud computing has created the most profound shift in information technology in recent memory. Leveraging cloud technology, companies can build, deploy, and scale their applications faster than ever. But the adoption of cloud native tools and processes also brings new security challenges. Between complex cloud infrastructure and the expansion of cloud-based services, malicious actors have access to a bigger attack surface than they did even a few years ago.
How Spotify uses Snyk to secure the SDLC
Spotify’s engineering team recently published a blog discussing their use of Snyk to maintain security testing in the SDLC. The following is a recap of that blog written by Engineering Manager, Edina Muminovic. Spotify, a company known for employing thousands of world-class developers, needed to redraw its software development lifecycle, or SDLC.