Security Update: Transaction Reversal Fraud - UK Edition
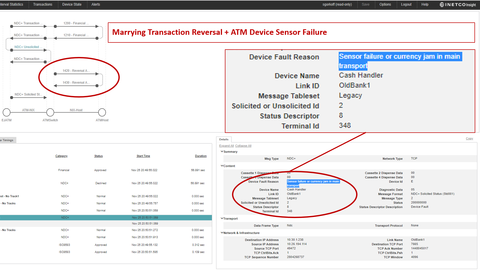
On November 21st, NCR issued a security alert for a new form of Transaction Reversal Fraud (TRF) occurring in the UK, typically between 10 PM and midnight on any given day. Contrary to previously reported TRF attacks in which cash is pried from the dispenser after a payment reversal is initiated due to the jamming of the card reader, this new method does not require any interaction with the card reader or the use of modified cards.