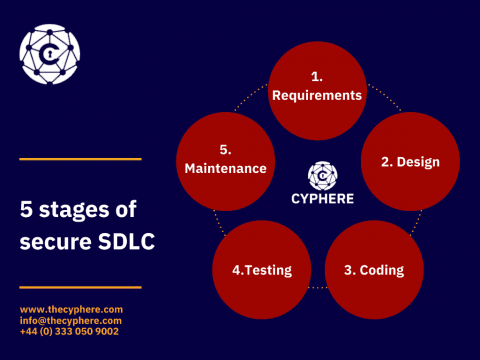
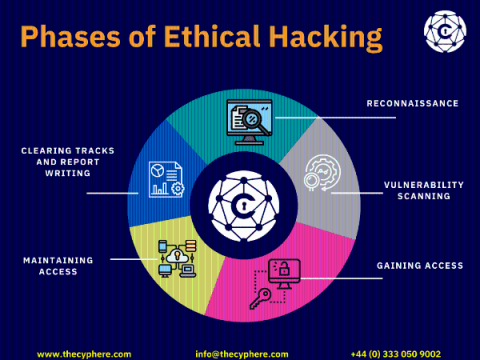
Secure software development lifecycle (SDLC) Best Practices
With all the remote works, online businesses, and digital lifestyle, applications (software) have become an integral part of our lives. In contrast, the growing rate of data breaches and cyber-attacks exploiting minor glitches in application functionality has diverted attention to application security which is still underrated in the era of phenomenal technological advancement.