Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cyphere
Azure Penetration Testing Service | Protect Your Cloud Applications Now
Cloud Penetration Testing Service: Safeguarding Your Digital Fortresses
CREST penetration testing guide and methodology
Penetration testing is an important component of the security strategy of any organisation. A well-conducted pen test can help IT teams ensure that their defences are up to par and are capable of protecting businesses and organisations against cyber security attacks.
CREST Certification benefits, cost, OSCP equivalent and other details
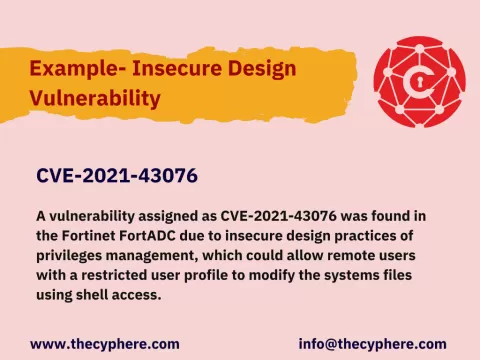
Insecure design vulnerabilities - what are they, and why do they occur?
Healthcare Cyber Attack Statistics
As technology has advanced and the world has become more interconnected, the threat of cyber-attacks has become a significant concern for businesses, smaller healthcare organisations, governments, civil rights and individuals alike. While cyber-attacks can target any sector, healthcare organisations have become an increasingly attractive target for cybercriminals in recent years.
Malware statistics to be taken seriously in 2023
We live in a digital age, where new technologies are emerging daily, and old technologies are evolving and merging into new ones so fast that one could quickly lose track. All of this new technology is for the betterment and ease of life and to ensure that humanity lives a peaceful, stress-free and non-redundant life.
Cyber Insurance Statistics - Payouts, Claims and Facts 2023
A data breach may not only damage your computer system or IT infrastructure, but it may also destroy your brand reputation. The consequences of a data breach may be very horrific, which may lead organisations, whether they be large companies or small businesses, to bankruptcy.
Social engineering statistics you must know
It is rightly said that the weakest link, even in a most cyber-secure environment, is the human being which renders the entire organisation as vulnerable as the weakest link. Playing games with the human mind and manipulating human thinking and psychology is extremely easy; hence, the human being is the lowest asset in a secure cyber environment.