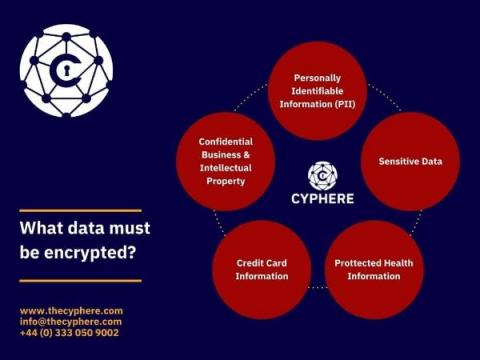
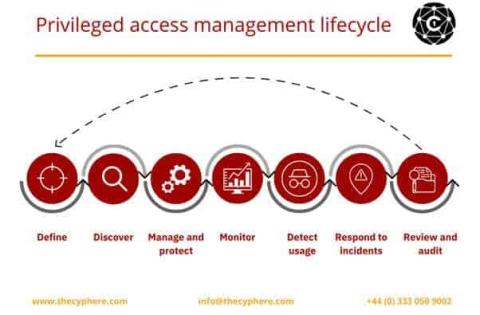
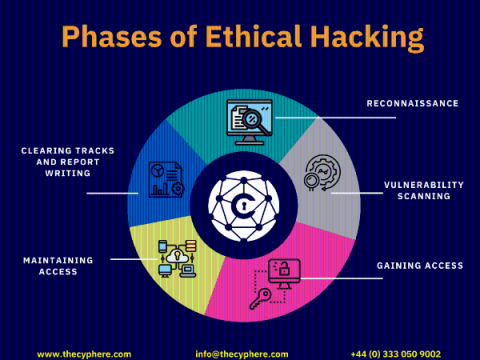
What is DHCP? Dynamic Host Configuration Protocol Guide
Without DHCP, it is difficult to imagine how we would be able to connect to the internet or our local network. DHCP is a vital part of how our devices on IP networks communicate with each other and the world around us. This article will cover DHCP in-depth, explaining what it is, how it works, its components, logging, configuration, and its benefits.