Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Why Enterprise Digital Rights Management (EDRM) has an edge over Data Loss Prevention (DLP)?
WhiteSource Customer Success Story - Open Raven
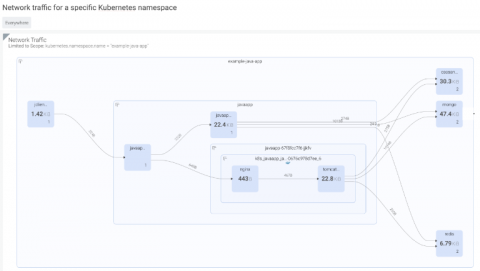
NIST 800-53 compliance for containers and Kubernetes
In this blog, we will cover the various requirements you need to meet to achieve NIST 800-53 compliance, as well as how Sysdig Secure can help you continuously validate NIST 800-53 requirements for containers and Kubernetes.
Announcing Netskope's Upcoming Integration for Splunk Mission Control
Today’s security operations require coordinated efforts from multiple team members, many of whom are in different roles and technology specializations. Complexity inhibits the ability to conduct time-sensitive operations such as incident response. Security engineers and the threat hunters have to be on the same page when it comes to establishing priorities and conducting investigation, across the entire detection & response lifecycle.
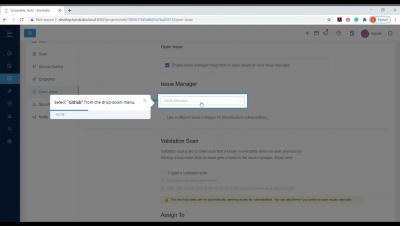
Session Control for SSH and Kubernetes in Teleport 4.4
Teleport 4.4 is here! The major innovation we’re introducing in this version is much improved control over interactive sessions for SSH and Kubernetes protocols. We’ll do a deeper dive into session control later, but for those who aren’t familiar with it, Teleport is an open source project. It provides access to SSH servers and Kubernetes clusters on any infrastructure, on any cloud, or any IoT device, anywhere, even behind NAT.
Teleport 4.4: Concurrent Session Control & Session Streaming
A SSH session can be interactive or non-interactive. The session starts when a computer or human connects to a node using SSH. SSH sessions can be established using public/private key cryptography or can use short lived SSH Certificates, similar to how Teleport works. Organizations often want to know who is accessing the systems and provide a greater level of control over who and when people are accessing them, which is where Teleport 4.4 comes into play.
Website Security: How to Protect Your Website Checklist
Putting a website on the internet means exposing that website to hacking attempts, port scans, traffic sniffers and data miners. If you’re lucky, you might get some legitimate traffic as well, but not if someone takes down or defaces your site first. Most of us know to look for the lock icon when we're browsing to make sure a site is secure, but that only scratches the surface of what can be done to protect a web server.
What is SQL injection?
An SQL injection (also known as SQLi) is a technique for the “injection” of SQL commands by attackers to access and manipulate databases. Using SQL code via user input that a web application (eg, web form) sends to its database server, attackers can gain access to information, which could include sensitive data or personal customer information. SQL injection is a common issue with database-driven websites.