Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Cybersecurity Hygiene: Not a Dirty Little Secret for Long
In October 2018, FICO (a consumer credit scoring specialist) began scoring the cybersecurity of companies based upon a scan of internet facing vulnerabilities. FICO grades companies using the same scoring that is familiar with consumer credit. These metrics are then used to compare security risks against competitors. This announcement has the potential to be a sea change event in cybersecurity.
How to Initiate a Threat Hunting Program (Part 2)?
In the previous steps, analysts have gathered enough data to answer their hypothesis. Two types of situations can occur. Either the real threat is found or the vulnerability is detected. In both cases, analysts action is necessary. The analysts must respond immediately when a real threat is identified. However, if there is any vulnerability, they should also resolve this before it becomes a really big nightmare.
Serverless vs Cloud vs On-prem
Server architecture can differ in a lot of ways, but the three main categories would be on-prem, cloud and serverless. Some believe that cloud and serverless can be used interchangeably, which is not the case. To help clear up some confusion, this blog post will explain each of them and how it affects the security work.
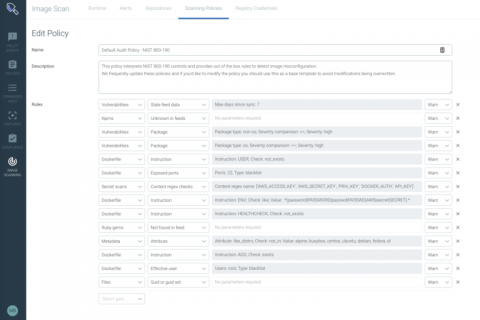
Detectify security updates for 7 March
For continuous coverage, we push out major Detectify security updates every two weeks, keeping our tool up-to-date with new findings, features and improvements sourced from our security researchers and Crowdsource ethical hacker community. Due to confidentially agreements, we cannot publicize all security update releases here but they are immediately added to our scanner and available to all users. This post highlights a few things that we have improved in the last two weeks.
Better together with Sysdig and Anchore: Comprehensive container security across the software development lifecycle
In the new cloud-native world, ephemeral services like containers make security a challenging task. As enterprises start adopting containers in production, they suffer from a great deal of variance in the software, configuration, and other static artifacts that exist across their organization’s container image set.
Weekly Cyber Security News 08/03/2019
A selection of this week’s more interesting vulnerability disclosures and cyber security news. In the new GDPR age we are in, exploration of data at rest has been high on the agenda for many, and this item perked my interest – and some concern. Well worth a read.
Kubernetes Security-Are your Container Doors Open?
Container adoption in IT industry is on a dramatic growth. The surge in container adoption is the driving force behind the eagerness to get on board with the most popular orchestration platform around, organizations are jumping on the Kubernetes bandwagon to orchestrate and gauge their container workloads.
Machine data processing and 5G, IoT, and AI at Mobile World Congress 2019
One thing that’s become evident to me after years attending Mobile World Congress is that, in fact, there are several events running in parallel, with a few common denominators: network technology providers, device manufacturers, telecom operators, and services companies all come to Barcelona to present and demonstrate the latest and greatest of the year’s dominating trends.
Announcing the AlienVault Success Center!
We are very excited to announce that our new Success Center has just launched. It is our new “one stop shop” for help for AT&T Cybersecurity commercial USM Anywhere, USM Appliance and USM Central customers, OTX and OSSIM users, and InfoSec practitioners in need of help and support.