Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Hunting
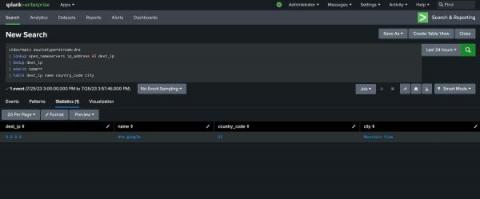
Threat hunting with Sumo Logic: The Command Line
Using Splunk Stream for Hunting: Finding Islands in the Stream (of Data)
Using the Lookup Command for Threat Hunting (Lookup Before You Go-Go)
Using Threat Hunting to Uncover Cybersecurity Threats
In the fast-evolving digital landscape, the prevalence of cyber threats has become a stark reality for businesses and individuals alike. The conventional cybersecurity measures, while essential, are often reactive and inadequate against sophisticated attacks. This is where Threat Hunting emerges as a proactive and dynamic approach to cybersecurity. In this blog, we delve into the fascinating world of Threat Hunting and explore its significance in safeguarding against cyber adversaries.
Turning Hunts Into Detections with PEAK
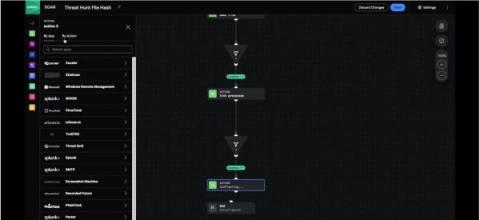
Splunk SOAR Playbook of the Month: Threat Hunting with Playbooks
What is Cyber Threat Hunting?
Cyber threat hunting is a proactive security strategy that involves searching for threats within a network before they can cause significant damage. Unlike traditional methods, which are reactive and wait for an alert before taking action, threat hunting seeks to actively identify and mitigate hidden threats that have evaded initial security measures. Threat hunting involves constant monitoring and data analysis to spot suspicious behavior that may indicate a cyber attack.