DNS Over HTTPS: Facts You Should Know
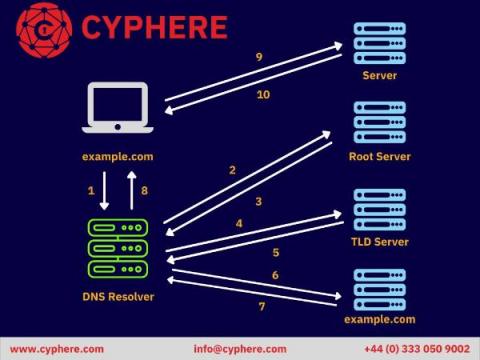
A new protocol, DNS over HTTPS (DoH), is a sensation in modern times, designed for enterprise security products and policies. A combination of DNS protocol and HTTPS protocol, DoH affects businesses, organisations, and regular users. DNS over HTTPS is used to enhance the security of network communication.