Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
Best practices for reducing sensitive data blindspots and risk
Modern applications log vast amounts of personal and business information that should not be accessible to external sources. Organizations face the difficult task of securing and storing this sensitive data in order to protect their customers and remain compliant. But there is often a lack of visibility into the sensitive data that application services are logging, especially in large-scale environments, and the requirements for handling it can vary across industries and regions.
Coffee Talk with SURGe: 2022-APR-19 MS-RPC Vulnerability, Lazarus, Pipedream
The Upsurge in Ransomware Attacks in Australia and Opportunities to Protect Data
There are rare occasions when you open the news and don't find anything about cybersecurity in the headlines. According to the Australian Cyber Security Centre (ACSC), Australia has dealt with a cyberattack every 8 minutes in the financial year 2020-21, with over 67,500 cases of cybercrime registered in the same year. Studies indicate that ransomware is one of the most frequent and damaging types of malware leveraged by cybercriminals.
Explore Corelight evidence in Humio Community Edition
Now available: A free and easy way to learn about Humio and Corelight. As part of our alliance partnership with CrowdStrike and Humio, Corelight is excited to announce a new collaboration that allows our customers and the community to experience the value of evidence.
Tools for Threat Hunting and IT Service Risk Monitoring
STRT-TA03 CPE - Destructive Software
The Splunk Threat Research Team is monitoring several malicious payloads targeting Customer Premise Equipment (CPE) devices. These are defined as devices that are at customer (Commercial, Residential) premises and that provide connectivity and services to the internet backbone. Examples include.
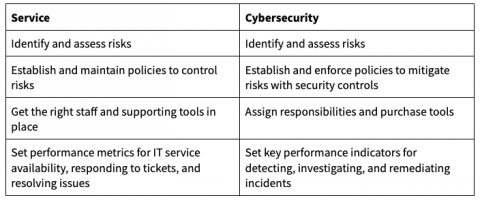
Use Service Design in Operations Management to Enhance Security
State of Security Research Details Essential Strategies for the Year Ahead
This year, security teams face more challenges — old and new — and grapple with high rates of burnout. Cloud complexity, supply chain attacks and additional obstacles are pushing security teams to the limits, and inspiring new responses. New research points to key strategies that will help organizations weather the complex challenges and attacks ahead.
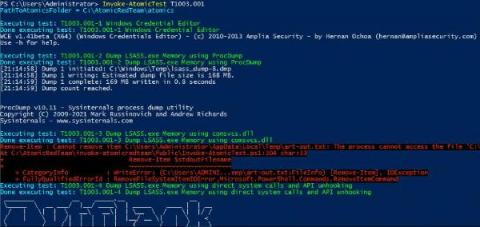
You Bet Your Lsass: Hunting LSASS Access
One of the most commonly used techniques is to dump credentials after gaining initial access. Adversaries will use one of many ways, but most commonly Mimikatz is used. Whether it be with PowerShell Invoke-Mimikatz, Cobalt Strike’s Mimikatz implementation, or a custom version. All of these methods have a commonality: targeting LSASS.