Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
Graylog Security - The Affordable SIEM Alternative
CrowdStrike Introduces Humio for Falcon, Redefining Threat Hunting with Unparalleled Scale and Speed
Making a Business Case for the Right SIEM
Let’s admit it — switching to a new SIEM can be tough. And expensive. But even when it isn’t tough or expensive, it’s always scary.
Truth in Malvertising?
Splunk SURGe recently released a whitepaper, blog, and video that outline the encryption speeds of 10 different ransomware families. Early in our research, during the literature review phase, we came across another group that conducted a similar study on ransomware encryption speeds. Who was this group you ask? Well, it was actually one of the ransomware crews themselves.
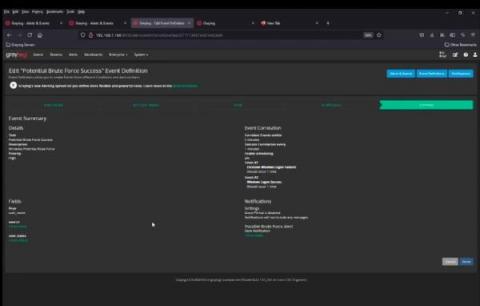
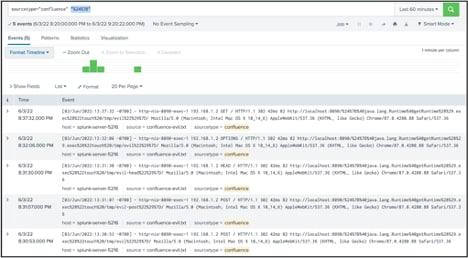
Atlassian Confluence Vulnerability CVE-2022-26134
If you want just to see how to find evidence of the Atlassian vulnerability in your Confluence systems, skip down to the “detections” sections. Otherwise, read on for a quick breakdown of what happened, how to detect it, and MITRE ATT&CK mappings.
Meet Devo SciSec
Centralized Log Management for Security and Compliance
Centralized Log Management for Access Monitoring
Get Extended Security Insights from Chrome Browser with Splunk
The way we work has drastically changed since the start of the pandemic. With more companies adopting remote and hybrid work models, there has been a 600% increase in cybercrime and 65% of organizations have seen a measurable increase in attempted cyberattacks, which is particularly problematic since 78% say remote workers are harder to secure.