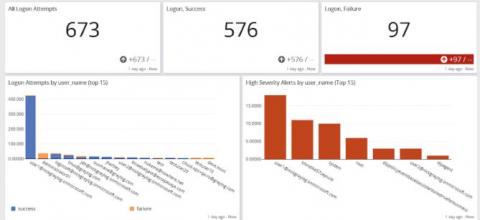
Splunk Assist: Cloud-Powered Insights Just for You, at Your Fingertips
Have you been worried about whether your deployment is secure? Are you tired of keeping track of all security vulnerabilities and vendor-provided patches to ensure that your exposure to such vulnerabilities is minimized? What about making sure that the certificates for your hundreds of forwarders, indexers, search heads and other Splunk connectors are not expired? You’re not alone!