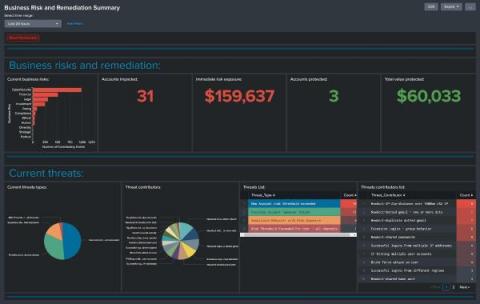
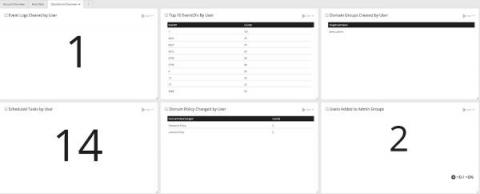
Federated Search for Security
Splunk introduced Federated Search in July 2021 to much fanfare. We won’t go into too much detail about how it works because there is already a great writeup in a previous blog along with Splunk Federated Search documentation.