Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
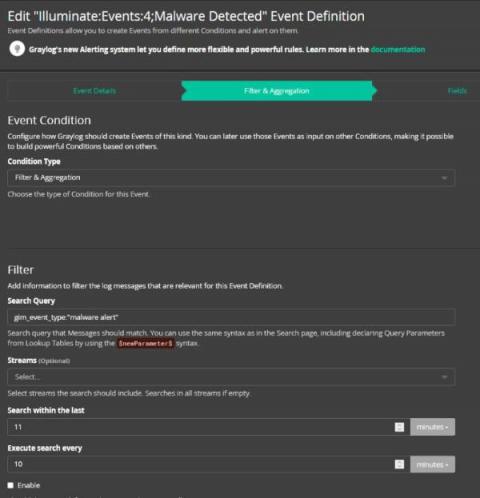
Log Management Strategy for Cybersecurity Maturity
CrowdStrike and Google Chrome: Building an Integrated Ecosystem to Secure Your Enterprise Using the Power of Log Management
Organizations today face an onslaught of attacks across devices, identity and cloud workloads. The more security telemetry an organization has to work with, the better threat hunters can contextualize events to find and remediate potential threats. Google recently announced Chrome Enterprise Connectors Framework, a collection of plug-and-play integrations with industry-leading security solution providers.
Searching Data: List View
Coffee Talk with SURGe: DOJ China Espionage, Drizly Complaint, Text4Shell, U.S. Midterm Elections
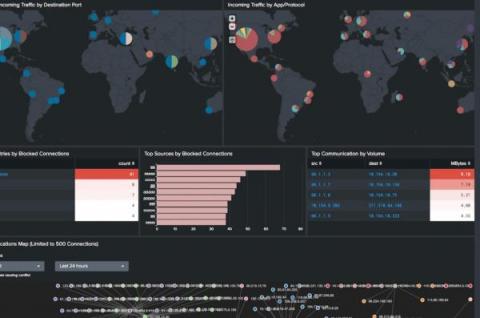
Splunk Security with the Infosec App
There's so much that can be accomplished with Splunk’s security tools. Today, we are going to focus on all the benefits of the InfoSec App for Splunk. The InfoSec app — which is an entitlement to Splunk customers — is powered by the Splunk platform, and relies on accelerated data models and the Common Information Model (CIM) to provide a consistent and normalized view into the event data that you’ll bring into Splunk.
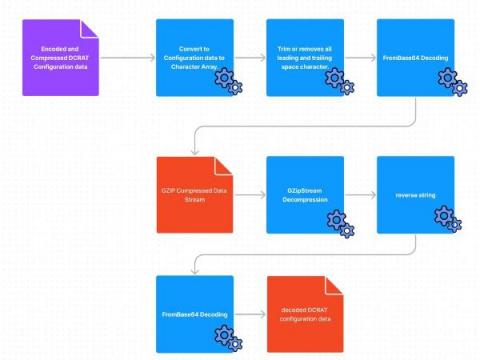
Dark Crystal RAT Agent Deep Dive
The Splunk Threat Research Team (STRT) analyzed and developed Splunk analytics for this RAT to help defenders identify signs of compromise within their networks. Remote Access Trojans (RATs) are one of the most common tools used by threat actors as a malicious payload to attack targeted hosts and steal information. One example is the Dark Crystal RAT (DCRat) that is capable of remote access, post exploitation and data exfiltration.
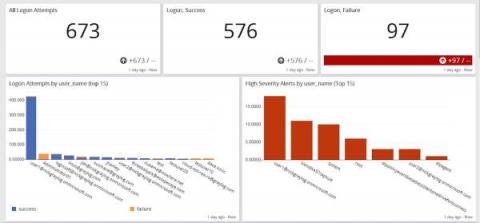
New SOC Performance Report: Security Analysts Are Overworked and Under Resourced
The fourth annual Devo SOC Performance ReportTM shows security professionals believe the SOC is significant to their organization’s cybersecurity strategy. As noted in our last blog, 77% of respondents say their SOC is “very important” or “essential” to their organization. But there’s pain behind the scenes as well. The report notes the majority of security professionals are feeling overwhelmed due to too much work and not enough resources.