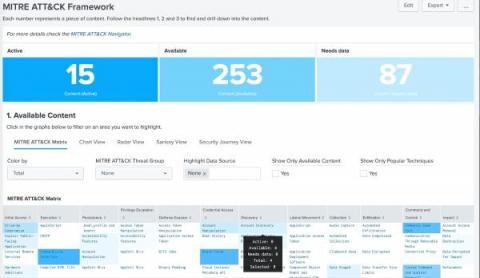
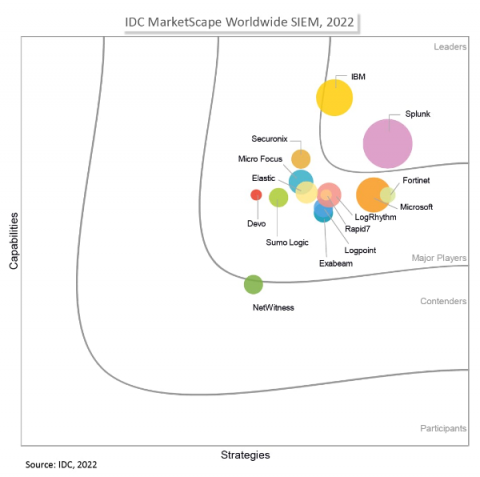
Devo Recognized as a Major Player by IDC MarketScape
SIEMs have come a long way since they first debuted in the security operations center (SOC) well over a decade and a half ago. Today, next-gen SIEMs are far more advanced than early systems, which merely gathered and logged data from different sources. Now, SIEM software can deliver comprehensive insight into network security and data protection by looking for anomalous activity that could indicate compliance, performance and security issues.