Shift Left Security: How To Shift Security Left for Software Development
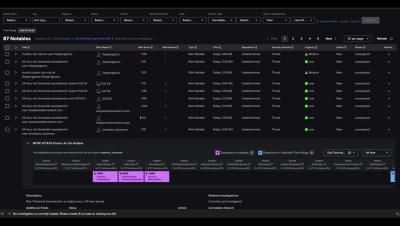
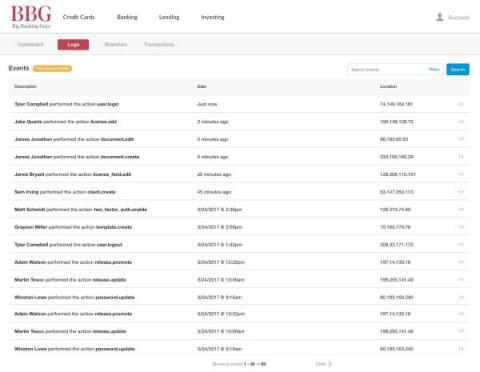
For a long time, security and development were two distinct aspects of programming. As organizations started to leverage software and technology as differentiating factors, the speed and quality of development became more important than ever. Organizations no longer had time after development was complete to address security vulnerabilities. Catching vulnerabilities too late opens companies up to unnecessary risk and can be costly to fix.