Use Kubescape to check if your Kubernetes clusters are exposed to the latest K8s Symlink vulnerability (CVE-2021-25741)
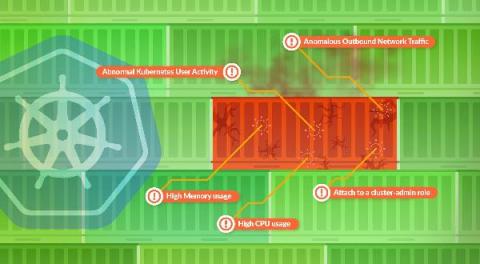
A new HIGH severity vulnerability was found in Kubernetes in which users may be able to create a container with subpath volume mounts to access files & directories outside of the volume, including on the host filesystem. The issue is affecting the Kubelet component of Kubernetes (Kubelet is the primary "node agent" that runs on each node. It registers the node with the apiserver and launches PODs on it).