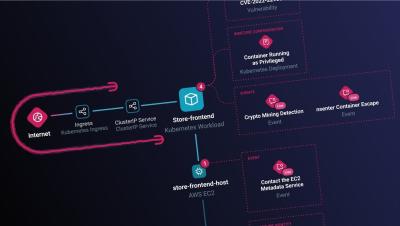
Detecting and mitigating CVE-2023-4911: Local Privilege Escalation Vulnerability
Recently, Qualys discovered and reported a critical vulnerability affecting the popular GLIBC ecosystem, which is installed by default on most Linux-based operating systems. Specifically, a buffer overflow was found in the code responsible for handling special environment variables during the startup of a process which can result in a local privilege escalation. Fortunately, exploitation of this vulnerability can be detected by Falco.