Enable Kubernetes Pod Security Policy with kube-psp-advisor
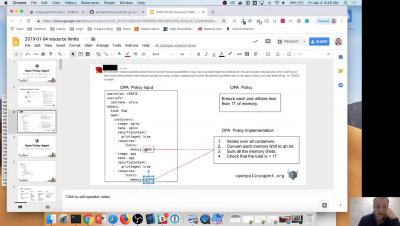
Kubernetes Pod Security Policy is a mechanism to enforce best security practices in Kubernetes. In this tutorial, we will explain how to enable Kubernetes Pod Security Policy across your cluster using kube-psp-advisor to address the practical challenges of building an adaptive and fine-grained security policy on Kubernetes in production.