Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
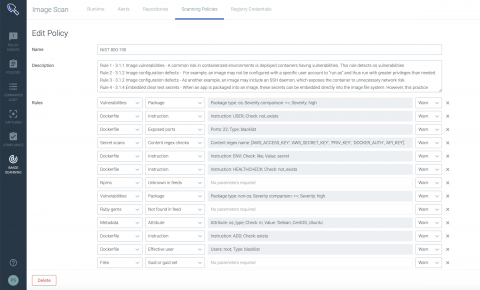
NIST SP 800-190 application container security with Sysdig Secure
In September 2017, the National Institute of Standards and Technology (NIST) released Special Publication (SP) 800-190, Application Container Security Guide. NIST SP 800-190 explains the security concerns associated with container technologies and recommendations for the image details and container runtime security. It provides prescriptive details for various sections including image, registry, orchestrator, container and host OS countermeasures.
Announcing the Sysdig Cloud-Native Visibility + Security Platform 2.0
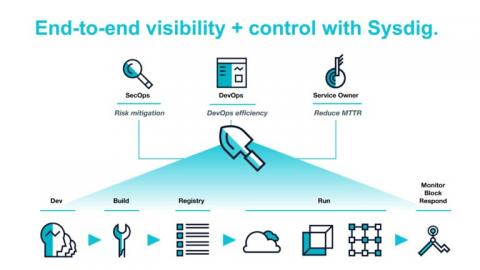
Today we’re announcing version 2.0 of the Sysdig Cloud-Native Visibility + Security platform. It provides a more powerful and significantly simpler way for enterprises to see the health, risk, and performance of their cloud-native environments in a single unified view.
Understanding "container security"
Do you docker? Without a doubt, containers are one of the hottest concepts in application delivery and security these days. And that’s a very good thing. Containers have tremendous advantages over the way we have done things in the past. But how should containers influence a threat detection and response strategy? Do I need a larger “container security” strategy to get started deploying my apps using container architectures?
What Your Kubernetes Security Checklist Might Be Missing
New technologies often require changes in security practices. What is remarkable about containers and Kubernetes, is that they also provide the potential for enhancing and improve existing security practices. In this post, I will share a model that we use at Nirmata to help customers understand security concerns and plan Kubernetes implementations that are secure.
Zero Trust Security: Supporting a CARTA approach with Continuous Monitoring
Container compliance for Docker and Kubernetes
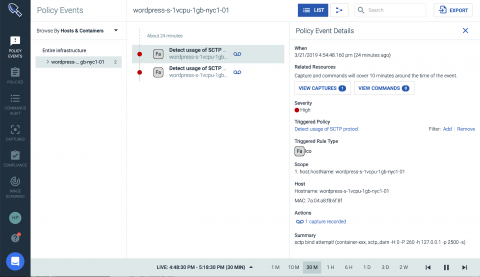
Detecting and preventing cgroups escape via SCTP - CVE-2019-3874
This week CVE-2019-3874 was discovered which details a flaw in the Linux kernel where an attacker can circumvent cgroup memory isolation using the SCTP socket buffer. In containerised environments, this has the potential for a container running as root to create a DoS.
The Myth of a Single Container Security Solution
A proper container security strategy involves evaluating all components in the system.
Detecting the Kubernetes API Server DoS Vulnerability (CVE-2019-1002100)
Recently, a new Kubernetes related vulnerability was announced that affected the kube-apiserver. This was a denial of service vulnerability where authorized users with write permissions could overload the API server as it is handling requests. The issue is categorized as a medium severity (CVSS score of 6.5) and can be resolved by upgrading the kube-apiserver to v1.11.8, v1.12.6, or v1.13.4.